

KKCSI will migrate your WordPress websites from your existing hosting.
Free of charge.
All Hosting plans are backed by industry leading DDoS protection to keep your website online.
We use JetBackup to perform random full account backups to keep all your files, email and databases safe. Free unlimited Restoration.
We offer the Softaculous 1-click installer to easily install popular apps such as WordPress, Joomla and many more!
Detects all malicious files, including trojan backdoors, web-shells, viruses, hacker tools, 'Blackhat' SEO, Scripts, phishing pages and etc.
You can send upto 500 emails per hour. Most of the other web hosting companies only allow 100 to 200 outgoing emails per hour.


SitePad is a drag and drop website builder with more than 850 Professional Themes which cover a wide range of categories like Blog, Business, Portfolio, Restaurants, Travel, etc and 40+ Widgets like Image/Video Slider, Image Galleries, Rich Text, Video, Audio, Service Box, Google Maps, Contact Form, Social Media and many more.
Want to make blogging site or website for your Business or Restaurant? We have themes to cater all your needs by covering wide range of categories like Blog, Business, Portfolio, Restaurants, Travel and many more !!
All themes are Responsive, styles and look can be customized from the Website Editor.
Add an Image/Video Slider to your website using Sliders Widget, add long text using Rich Text, Quote your content using the Quotes widget, add Social Media features using Social Media widget or build Graphs and Pie charts using the Charts widget.
Build your website using simple Drag and Drop widgets like Image/Video Slider, Image Galleries, Rich Text, Video, Audio, Service Box, Google Maps, Contact Form, Social Media Buttons, Call To Action, Grid Gallery and many more!!

Managed WordPress Hosting is a type of web hosting service that is specifically designed to cater to the needs of WordPress websites. It is a premium hosting service that provides users with a hassle-free experience by taking care of all the technical aspects of running a website. This includes tasks such as WordPress installation, software updates, security, backups, and performance optimization. With Managed WordPress Hosting, users can focus on creating content, marketing their website, and serving their visitors.
Benefits of Managed WordPress Hosting
There are several benefits of using Managed WordPress Hosting, including:
Speed and Performance
Managed WordPress Hosting is optimized for running WordPress websites, which means faster loading times. This is a huge factor in user experience and SEO.
Scalability: Managed WordPress Hosting normally scales better than other types of hosting. This is good news for when your site keeps growing!
Security: Managed WordPress Hosting providers offer robust security features to protect your website from hackers and malware.
Customer Support: Managed WordPress Hosting providers offer expert WordPress support, which means you can get help with any issues related to your website.
Custom Hosting Dashboards: Managed WordPress Hosting providers offer custom hosting dashboards that make it easy to manage your website.
How to Choose the Best Managed WordPress Hosting Service for Your Website
Choosing the best Managed WordPress Hosting service for your website can be a daunting task. Here are some factors to consider when choosing a Managed WordPress Hosting service:
Uptime: Look for a Managed WordPress Hosting service that offers at least 99% uptime.
Speed: Look for a Managed WordPress Hosting service that offers fast load times.
Security: Look for a Managed WordPress Hosting service that offers robust security features.
Customer Support: Look for a Managed WordPress Hosting service that offers 24/7 customer support.
Price: Look for a Managed WordPress Hosting service that offers a good balance between price and features.
Conclusion
In conclusion, Managed WordPress Hosting is a premium hosting service that provides users with a hassle-free experience by taking care of all the technical aspects of running a website. There are several benefits of using Managed WordPress Hosting, including speed and performance, scalability, security, customer support, and custom hosting dashboards.
Yes, Malaysia is generally considered a safe location for hosting websites and emails. The country has a stable political and economic environment, reliable infrastructure, and advanced technology infrastructure, making it a viable option for website and email hosting.
Malaysia is a country located in Southeast Asia, known for its diverse culture, vibrant cities, and lush landscapes. When it comes to website and email hosting, Malaysia is generally considered a safe location due to its stable political and economic environment, reliable infrastructure, and advanced technology infrastructure.
Malaysia has a well-developed internet infrastructure with widespread internet connectivity and multiple data centers that are equipped with modern technology and security measures. These data centers are often managed by reputable hosting providers that offer a wide range of hosting services, including shared hosting, virtual private server (VPS) hosting, dedicated servers, and cloud hosting.
When it comes to data security, choosing a reliable hosting provider is crucial. Reputable hosting providers in Malaysia typically implement industry-standard security measures to protect websites and emails from unauthorized access and data breaches. These measures may include firewalls, SSL certificates, data encryption, regular backups, and other security protocols.
It's important to note that website and email hosting security is not solely dependent on the location, but also on the security measures implemented by the hosting provider and the website or email platform itself. Therefore, it's crucial to select a reputable hosting provider that has a proven track record of reliability, performance, and security.
When choosing a hosting provider in Malaysia or any other location, conducting thorough research, reading customer reviews, and comparing different providers can help you make an informed decision. Look for providers that offer robust security features, reliable performance, excellent customer support, and competitive pricing.
In addition to hosting provider security measures, it's also important to keep your website and email platform updated with the latest security patches and follow best practices for data security. This includes using strong passwords, enabling two-factor authentication, keeping software and plugins up-to-date, and regularly backing up your website and email data.
In summary, while Malaysia is generally considered a safe location for hosting websites and emails, it's crucial to choose a reputable hosting provider that implements robust security measures to ensure the safety and security of your website and email data. Regularly updating your website and email platform and following best practices for data security are also essential for maintaining a secure hosting environment.
cPanel is a popular web-based control panel used for managing websites and hosting accounts. It provides a graphical user interface (GUI) that allows website owners and web hosting providers to easily manage various aspects of their websites and hosting accounts, such as domain management, file management, email management, database management, security settings, and more.
cPanel is known for its user-friendly interface, making it accessible to both technical and non-technical users. It provides a wide range of tools and features that simplify website management tasks and enable website owners to have greater control over their hosting accounts without requiring extensive technical knowledge.
Some of the key features of cPanel include:
1) Domain management: cPanel allows users to manage multiple domain names, subdomains, and add-on domains, including domain registration, DNS management, and domain redirection.
2) File management: cPanel provides a file manager that allows users to upload, download, and manage files on their website's server, as well as set file permissions, create and edit files, and manage FTP accounts.
3) Email management: cPanel enables users to create and manage email accounts, set up email forwarding, configure email filters, set up mailing lists, and manage email spam filters.
4) Database management: cPanel provides tools for creating and managing MySQL databases, including creating and deleting databases, managing database users, and performing database backups and restorations.
5) Security settings: cPanel includes security features such as SSL certificate management, IP blocking, password protection for directories, and more, to help users secure their websites and hosting accounts.
6) Website statistics: cPanel provides various web statistics tools, such as AWStats and Webalizer, which allow users to monitor and analyze website traffic, visitor behavior, and other performance metrics.
7) Software installations: cPanel includes a built-in tool called Softaculous that allows users to easily install popular web applications, such as WordPress, Joomla, Drupal, and others, with just a few clicks.
cPanel is widely used by web hosting providers as a standard control panel for managing hosting accounts, and it is compatible with various operating systems, including Linux and Windows. It is known for its extensive documentation, community support, and regular updates, which make it a reliable and popular choice for managing websites and hosting accounts.
Disk space refers to the amount of storage capacity available on a server's hard disk drive (HDD) or solid-state drive (SSD) for storing files, data, and content associated with a website or web application. It is typically measured in units of bytes, such as gigabytes (GB), terabytes (TB), or petabytes (PB).
Disk space is a crucial resource for hosting websites and web applications, as it determines the amount of data that can be stored on the server. It includes various types of data, such as website files, databases, email accounts, multimedia files, logs, and other content associated with the hosted website or application.
Website files, including HTML, CSS, JavaScript, images, videos, and other media files, are stored on the server's disk space. Databases, such as MySQL or PostgreSQL databases, are used to store dynamic website content and are also stored on the disk space. Email accounts associated with a hosted domain also consume disk space for storing email messages, attachments, and other data.
Disk space requirements vary depending on the size and complexity of a website or web application. Smaller websites with fewer files and lower traffic may require only a few gigabytes of disk space, while larger websites or web applications with extensive multimedia content and high traffic may require terabytes or more of disk space.
It's essential to consider the disk space offered by a web hosting provider when selecting a hosting plan for a website or web application. It's important to ensure that the hosting plan provides enough disk space to accommodate the current and future storage needs of the website or application. Disk space usage should be monitored regularly to avoid exceeding the allocated storage limits, which could result in website performance issues or additional charges from the hosting provider.
In addition to disk space, other factors such as bandwidth, CPU resources, RAM, and other hosting resources should also be considered when selecting a hosting plan, as they collectively impact the overall performance and reliability of a website or web application.
Bandwidth refers to the maximum amount of data that can be transmitted over a network connection in a given period of time. It is typically measured in bits per second (bps), kilobits per second (kbps), megabits per second (Mbps), or gigabits per second (Gbps). Bandwidth determines the speed at which data can be transferred between devices or over the internet.
Bandwidth is an important factor in determining the performance and speed of data transfer over a network. A higher bandwidth allows for faster data transfer rates, while a lower bandwidth results in slower data transfer rates. Bandwidth is often used as a measure of the capacity of a network connection or a hosting plan, as it determines how much data can be transmitted simultaneously.
Bandwidth is commonly used in various contexts, such as internet service providers (ISPs) providing internet plans with different bandwidth levels, web hosting providers offering hosting plans with different bandwidth limits, and in networking equipment specifications. Bandwidth is also relevant in various applications, such as streaming video, online gaming, file transfers, and other data-intensive tasks that require fast and reliable data transfer.
It's important to note that bandwidth is different from data usage or data transfer, which refers to the actual amount of data that is transmitted over a network connection. Bandwidth represents the capacity or potential of the network connection, while data usage refers to the actual amount of data that is transferred during a specific time period.
In summary, bandwidth refers to the maximum amount of data that can be transmitted over a network connection in a given period of time and is an important factor in determining the performance and speed of data transfer over networks. It is commonly used in various contexts, such as internet plans, hosting plans, and networking equipment specifications.
WordPress is a popular and widely used content management system (CMS) that allows users to create and manage websites, blogs, and online content. It is an open-source software, which means it is freely available for anyone to use, modify, and customize according to their needs.
WordPress provides a user-friendly interface and a range of tools and features that make it easy for individuals and businesses to create and manage websites without extensive technical knowledge or coding skills. Some key features of WordPress include:
1) Themes: WordPress offers a wide variety of themes, which are pre-designed templates that determine the appearance and layout of a website. Themes can be customized to suit the specific branding and design requirements of a website.
2) Plugins: WordPress has a vast library of plugins, which are add-ons that can be installed to extend the functionality of a website. Plugins allow users to add features such as contact forms, social media integration, e-commerce functionality, and more, without having to write custom code.
3) Content management: WordPress provides a user-friendly content management system that allows users to create, edit, and organize content, including text, images, videos, and more. Content can be organized using categories, tags, and other taxonomies for easy navigation and search.
4) SEO-friendly: WordPress is designed with built-in features that are optimized for search engine optimization (SEO), including customizable URLs, meta tags, and sitemaps, making it easier to improve the search engine visibility of a website.
5) User roles and permissions: WordPress allows multiple users with different roles and permissions to collaborate on a website, with options for administrators, editors, authors, contributors, and subscribers, each with different levels of access and capabilities.
6)Responsive design: WordPress themes are designed to be responsive, which means they adapt to different screen sizes and devices, including desktops, tablets, and mobile devices, providing a consistent user experience across various platforms.
7) Community and support: WordPress has a large and active community of users and developers who contribute to its development, provide support, and share resources such as themes, plugins, tutorials, and documentation.
WordPress is highly customizable, scalable, and versatile, making it suitable for a wide range of websites, from simple blogs to complex e-commerce websites, business websites, and more. It is a popular choice for website creation and management due to its ease of use, flexibility, and extensive ecosystem of themes and plugins.
Introduction:
In computing, an inode (short for "index node") is a data structure used by file systems to store information about a file or directory on a Unix-based operating system. Each file or directory has a unique inode number that identifies it on the file system. In this article, we will discuss what inode is, how it works, and its significance in the file system.
What is an inode?
An inode is a data structure that contains information about a file or directory on a Unix-based file system. It includes information such as the file's owner, permissions, creation and modification dates, and file size. In addition, it contains pointers to the blocks on the disk that hold the actual file data.
Inodes are a critical part of Unix-based file systems because they provide a way to access files and directories quickly and efficiently. Each inode has a unique identifier that is used by the file system to locate the file or directory on the disk.
How do inodes work?
When a file or directory is created on a Unix-based file system, an inode is created to store its metadata. The inode includes information about the file's owner, permissions, and timestamps, as well as pointers to the blocks on the disk that hold the file's data.
When a user requests to access a file, the file system uses the inode number to locate the inode on the disk. The inode is then used to retrieve the file's metadata and data blocks, which are read into memory and made available to the user.
Inodes also play a critical role in managing the file system's free space. When a file is deleted, its inode is marked as free, and the blocks that it was using are returned to the free space pool. The file system can then reuse these blocks for new files and directories.
Significance of inodes in the file system:
Inodes are an essential component of Unix-based file systems because they provide a way to access files and directories quickly and efficiently. Because each file and directory has a unique inode number, the file system can quickly locate and retrieve the metadata and data blocks associated with a particular file or directory.
In addition, inodes help manage the file system's free space by keeping track of which blocks are in use and which are free. When a file is deleted, its inode is marked as free, and the blocks it was using are returned to the free space pool. This ensures that the file system can efficiently reuse disk space, minimizing waste and maximizing available space for new files and directories.
Inodes also play a critical role in file system performance. Because inodes are used to access files and directories, the file system's performance is directly tied to the number of inodes available. If the file system runs out of inodes, it can no longer create new files or directories, which can lead to serious performance problems.
Conclusion:
Inode is a crucial data structure used by file systems to store information about files and directories on Unix-based operating systems. It provides a way to access files and directories quickly and efficiently, and also manages the file system's free space by keeping track of which blocks are in use and which are free. Inodes are critical to the performance of Unix-based file systems, and understanding how they work is essential for anyone working with these systems.
Sectigo is a leading global provider of digital certificates and web security solutions, offering a wide range of SSL/TLS certificates to secure websites, online applications, and communication channels. With a history dating back to 1998, Sectigo has established itself as a trusted name in the cybersecurity industry, providing reliable and comprehensive security solutions to businesses, organizations, and individuals worldwide.
One of the key offerings of Sectigo is its SSL/TLS certificates, which are used to encrypt communication between web browsers and web servers, ensuring that data transmitted over the internet is secure and protected from unauthorized access. SSL/TLS certificates establish a secure connection between a website visitor's browser and the website's server, encrypting the data that is transmitted, such as login credentials, credit card information, and other sensitive data. This helps to protect against eavesdropping, data breaches, and other forms of cyber attacks.
Sectigo offers a variety of SSL/TLS certificates designed for different use cases, including domain validation (DV), organization validation (OV), and extended validation (EV) certificates. DV certificates are the most basic type of SSL/TLS certificate and require only the domain ownership to be verified. They are typically used for personal websites, blogs, and small business websites. OV certificates, on the other hand, require a higher level of validation as they verify not only the domain ownership but also the organization's legal existence and legitimacy. OV certificates display the organization's name in the certificate details, providing an additional layer of trust for website visitors. EV certificates offer the highest level of trust and security among all the SSL/TLS certificates. They undergo the most rigorous validation process, including verification of the organization's legal existence, physical address, phone number, and other documentation requirements. EV certificates are recognized by the green address bar in web browsers, which prominently displays the organization's name, providing the highest level of trust for website visitors.
Apart from DV, OV, and EV certificates, Sectigo also offers other types of SSL/TLS certificates to meet various security needs. Wildcard certificates allow securing multiple subdomains under a single domain, making them cost-effective for websites with multiple subdomains. Multi-Domain certificates can secure multiple domains with a single certificate, making them ideal for websites with multiple domain names. Code Signing certificates are used to sign software and ensure its integrity, protecting against tampering and unauthorized modifications.
Sectigo's SSL/TLS certificates are widely trusted and recognized by all major web browsers, operating systems, and devices. They provide industry-standard encryption algorithms and key lengths, ensuring strong and robust encryption of data in transit. Sectigo also offers additional features such as daily website scanning for malware, vulnerability assessments, and site seals that can be displayed on websites to reassure visitors of their security.
In addition to SSL/TLS certificates, Sectigo offers a range of other web security solutions to protect against various cyber threats. These include Secure Email certificates for encrypting email communication, CodeGuard for website backup and malware monitoring, and Web Application Firewall (WAF) for protecting against web application vulnerabilities. Sectigo also provides solutions for IoT (Internet of Things) security, including device identity management and certificate lifecycle automation.
Sectigo has a strong customer base comprising businesses, organizations, and individuals across different industries, including e-commerce, finance, healthcare, government, and more. Its customers benefit from the comprehensive security solutions provided by Sectigo, helping to protect their websites, online applications, and communication channels from cyber threats.
In summary, Sectigo is a leading provider of digital certificates and web security solutions, offering a wide range of SSL/TLS certificates to secure websites and online applications. Sectigo's SSL/TLS certificates provide encryption, authentication, and trust, helping to protect against cyber threats and build customer confidence. With a history of expertise in the cybersecurity industry and a strong reputation for reliability and trust, Sectigo has become a trusted partner for businesses, organizations, and individuals worldwide.
One of the key advantages of Sectigo certificates is their compatibility and recognition by all major web browsers, operating systems, and devices. This ensures that website visitors using different browsers or devices will see the green padlock or the organization's name in the address bar, indicating a secure connection. This helps to build trust among website visitors, giving them the confidence to share sensitive information, such as credit card details or personal data, on websites protected by Sectigo certificates.
Sectigo also offers a user-friendly and efficient validation process for obtaining SSL/TLS certificates. The process is designed to be quick and easy, allowing businesses to secure their websites without undue delays. Domain validation (DV) certificates can be issued within minutes, while organization validation (OV) and extended validation (EV) certificates may require additional documentation and verification, but are still processed efficiently to ensure timely issuance.
Sectigo's SSL/TLS certificates also come with additional features that enhance website security. Daily website scanning for malware helps to detect and remove any malicious code that may have been injected into the website. Vulnerability assessments help to identify potential weaknesses in the website's security posture, allowing businesses to take proactive measures to address them. Site seals, which can be displayed on the website, provide a visible indication of the website's security, reassuring visitors of their safety.
Moreover, Sectigo offers a range of other web security solutions beyond SSL/TLS certificates. For example, Secure Email certificates ensure that email communication is encrypted, protecting sensitive information shared via email. CodeGuard provides website backup and malware monitoring, helping businesses quickly recover from any data loss or website compromise. The Web Application Firewall (WAF) protects against web application vulnerabilities, such as SQL injections and cross-site scripting (XSS) attacks. These additional solutions complement Sectigo's SSL/TLS certificates, providing comprehensive protection against various cyber threats.
In conclusion, Sectigo certificates are a trusted choice for businesses, organizations, and individuals seeking reliable web security solutions. With a wide range of SSL/TLS certificates to meet different needs, compatibility with major web browsers and devices, efficient validation process, and additional features for enhanced security, Sectigo has established itself as a leading provider of digital certificates and web security solutions. By securing websites and online applications with Sectigo certificates, businesses can protect their sensitive data, build customer trust, and safeguard their online reputation.
DirectAdmin is a web hosting control panel software that allows website owners and web hosting providers to manage and administer web hosting accounts and websites on a server. It provides a graphical user interface (GUI) that simplifies the management of web hosting services, making it easier for users to manage their websites, email accounts, databases, FTP accounts, and other hosting-related tasks.
DirectAdmin offers a wide range of features for website management, including domain management, file management, email management, database management, and DNS management, among others. Users can create and manage multiple websites, subdomains, and email accounts, set up FTP access, manage databases, and configure various web hosting settings using the DirectAdmin interface.
Some key features of DirectAdmin include:
1) User-friendly interface: DirectAdmin provides a user-friendly interface that makes it easy for website owners and web hosting providers to manage their hosting accounts and websites. The interface is designed to be intuitive and easy to navigate, even for users with limited technical knowledge.
2) Domain management: DirectAdmin allows users to manage multiple domain names and subdomains, including domain registration, DNS management, and domain redirection.
3) Email management: DirectAdmin provides tools for managing email accounts, including creating and managing email addresses, setting up email forwarders, and managing email quotas.
4) File management: DirectAdmin allows users to upload, manage, and organize files on their web hosting accounts using a web-based file manager.
5) Database management: DirectAdmin supports popular databases such as MySQL and PostgreSQL, allowing users to create, manage, and back up databases.
6) Security features: DirectAdmin includes various security features, such as SSL/TLS support, IP blocking, and password-protected directories, to enhance the security of hosted websites and accounts.
7) Customization options: DirectAdmin allows web hosting providers to customize the control panel interface and set up custom branding, providing a consistent and branded experience for their customers.
DirectAdmin is commonly used by web hosting providers as a hosting control panel solution for their customers, providing an easy-to-use interface for managing web hosting accounts and websites. It is compatible with various web hosting environments, including Linux-based servers, and is known for its stability, performance, and ease of use.
NVMe SSD stands for Non-Volatile Memory Express Solid-State Drive. It is a type of storage device that uses NAND flash memory technology to store data in a non-volatile manner, meaning that the data is retained even when power is turned off. NVMe SSDs are designed for high-speed data storage and retrieval, making them ideal for use in modern computers, servers, and data center environments.
NVMe is a newer storage interface protocol that is designed specifically for SSDs, offering higher performance and lower latency compared to traditional storage interfaces such as SATA (Serial ATA) and SAS (Serial Attached SCSI). NVMe SSDs connect to the computer or server using the PCIe (Peripheral Component Interconnect Express) interface, which provides faster data transfer speeds and improved overall performance.
One of the key features of NVMe SSDs is their ability to leverage the parallelism and performance of modern PCIe interfaces to deliver faster data transfer speeds and lower latency. NVMe SSDs can achieve significantly higher sequential and random read/write speeds compared to traditional storage interfaces, making them well-suited for applications that require high-speed data storage and retrieval, such as in gaming, multimedia production, virtualization, and big data processing.
NVMe SSDs also typically have a smaller physical form factor compared to traditional storage devices, which makes them ideal for use in smaller devices such as ultrabooks, tablets, and other mobile computing devices. They are also widely used in enterprise data centers and cloud computing environments, where high performance, low latency, and reliability are critical requirements.
In summary, NVMe SSDs are a type of high-performance solid-state drive that use the NVMe interface protocol to deliver faster data transfer speeds, lower latency, and improved overall performance compared to traditional storage interfaces. They are widely used in various applications where high-speed data storage and retrieval are required, including consumer devices, enterprise data centers, and cloud computing environments.
If a file system exceeds its inode limit, there can be several consequences:
Inability to create new files and directories: When a file system runs out of inodes, it cannot create new files or directories. This means that any application or user attempting to create a new file or directory will receive an error message indicating that the file system is full, even if there is still plenty of available disk space.
Performance issues: As the file system approaches its inode limit, its performance can degrade. This is because the file system has to spend more time searching for available inodes and allocating them to new files and directories. This can cause the file system to become slow and unresponsive.
Data loss: If the file system runs out of inodes and the application or user attempting to create a new file or directory does not handle the error correctly, data loss can occur. For example, if an application attempts to write data to a file and receives an "out of space" error, it may delete the file and any data that has already been written to it.
Difficulty in file system maintenance: If a file system reaches its inode limit, it can be difficult to perform routine maintenance tasks, such as creating backups, defragmenting the file system, or repairing file system errors. This is because these tasks require the file system to create new files and directories, which may not be possible if the inode limit has been reached.
Corruption of the file system: In rare cases, if a file system exceeds its inode limit and continues to be used, it can become corrupted. This is because the file system may start to reuse inodes that are still in use, leading to data corruption and file system errors.
Overall, running out of inodes can have serious consequences for the performance and reliability of a file system. Therefore, it is important to monitor inode usage and increase the inode limit as needed to prevent these issues.
Here are a few examples of situations where exceeding the inode limit can have negative consequences:
Web hosting: In a web hosting environment, each website typically has its own directory on the file system. If the inode limit is exceeded, the web server may be unable to create new files or directories for a website, which can cause the website to go offline or become unresponsive.
Large file systems: File systems that store a large number of files, such as media storage or file sharing systems, can quickly reach their inode limit. This can cause issues such as slow performance, inability to upload new files, or data loss.
Backup systems: Backup systems often rely on the file system's ability to create new files and directories to store backup data. If the inode limit is exceeded, the backup system may be unable to create new backup files, leading to incomplete backups and potential data loss.
Email servers: Email servers store a large number of individual email messages, each of which has its own file. If the inode limit is exceeded, the email server may be unable to store new messages, which can result in lost or bounced email.
Cloud storage: Cloud storage providers often allocate a certain amount of space to each user, but may not have a limit on the number of files that can be stored. If a user exceeds the inode limit, they may be unable to store new files, even if they have available storage space.
These are just a few examples of situations where exceeding the inode limit can have negative consequences. In general, any system that relies heavily on file creation or storage can be affected by inode limits. Therefore, it is important to monitor inode usage and increase the inode limit as needed to prevent these issues.
There are several advantages to using Gmail as the webmail to send and receive email with a domain email address:
Professional image: Using a domain email address with Gmail gives a more professional image compared to using a generic email address such as Gmail, Yahoo or Hotmail. This can be especially important for small businesses, entrepreneurs or freelancers who want to project a professional image to their clients or customers.
Large storage capacity: Gmail offers a large storage capacity for emails, which means you can store a lot of emails without worrying about running out of storage space. This is especially useful if you receive a lot of emails with attachments or if you need to keep a record of important correspondence.
Powerful search functionality: Gmail has powerful search functionality that allows you to quickly and easily find the email you need, even if you have a large number of emails in your inbox. This can be a huge time-saver compared to manually searching through your emails.
Easy integration with other Google services: Gmail is part of the Google suite of applications, which means it can be easily integrated with other Google services such as Google Drive, Google Calendar and Google Docs. This can help you to manage your work more efficiently and save time.
Security features: Gmail has advanced security features such as two-factor authentication and spam filtering, which can help to protect your email account from unauthorized access and spam emails.
Access from anywhere: Gmail is a web-based email service, which means you can access your emails from anywhere with an internet connection. This can be especially useful if you need to access your emails while on the go or when traveling.
Cost-effective: Using Gmail with a domain email address is a cost-effective solution, as it is often cheaper than using a dedicated email hosting service. This can be especially beneficial for small businesses or individuals who have a limited budget.
Overall, using Gmail as the webmail to send and receive email with a domain email address offers several advantages, including a professional image, large storage capacity, powerful search functionality, easy integration with other Google services, security features, accessibility from anywhere, and cost-effectiveness.
Is Gmail Safe?
Gmail is one of the most widely used email services in the world, with over 1.5 billion active users as of 2021. As a Google product, it has a reputation for being secure and reliable. In this article, we will explore the various security features that make Gmail a safe email service to use.
Encryption
One of the most important features that make Gmail safe is encryption. Gmail uses Transport Layer Security (TLS) to encrypt all email messages sent between Gmail servers and other email providers. TLS is an industry-standard protocol used to secure online communication and prevent eavesdropping or tampering.
When a Gmail user sends an email to someone using a different email provider, the email is encrypted in transit using TLS. This means that even if someone intercepts the email as it is being sent, they will not be able to read its contents.
In addition to encryption in transit, Gmail also provides encryption at rest. This means that emails are stored in encrypted form on Google's servers, making it more difficult for unauthorized access.
Two-Factor Authentication
Another key security feature of Gmail is two-factor authentication (2FA). With 2FA enabled, a user is required to provide a second form of identification in addition to their password to access their account. This could be a fingerprint, a code sent to their mobile device, or a physical security key.
2FA adds an extra layer of security to a user's account, making it much more difficult for someone to gain unauthorized access. Even if an attacker knows a user's password, they will not be able to access the account without also providing the second form of identification.
Spam Filtering
Gmail's spam filtering is another important security feature. Gmail has advanced algorithms that can detect and block spam emails before they reach a user's inbox. This helps to prevent users from being tricked by phishing emails or infected with malware.
Gmail's spam filter is not perfect, and some spam emails may still make it to a user's inbox. However, users can mark spam emails as such, which helps to train the spam filter to better recognize and block spam emails in the future.
Google's Security Team
Gmail is a product of Google, which means it benefits from Google's extensive security expertise. Google has a dedicated team of security experts who work to identify and fix security vulnerabilities in Gmail and other Google products.
Google's security team employs a range of measures to keep Gmail safe, including regular security audits, penetration testing, and bug bounties. They also work closely with other security researchers and organizations to stay up-to-date with the latest threats and vulnerabilities.
Privacy Settings
Gmail also has a range of privacy settings that allow users to control who can see their emails and data. For example, users can choose to enable "confidential mode," which allows them to set an expiration date for emails or require a passcode to access them.
Users can also control who has access to their Gmail account by managing their "connected apps" and "security settings." This allows users to revoke access for any apps or services that they no longer use or trust.
Data Backup and Recovery
Gmail also offers users the ability to backup and recover their emails and data. If a user accidentally deletes an email or loses access to their account, they can use Gmail's backup and recovery tools to restore their data.
Gmail automatically saves a copy of all sent and received emails to a user's "Sent" and "All Mail" folders, respectively. Users can also manually create backups of their Gmail data using the "Google Takeout" tool.
Conclusion
In summary, Gmail is a safe email service to use due to its advanced security features, including encryption, two-factor authentication, spam filtering, and Google's security team. In addition, Gmail's privacy settings
Maximum security and performance for your WordPress websites.
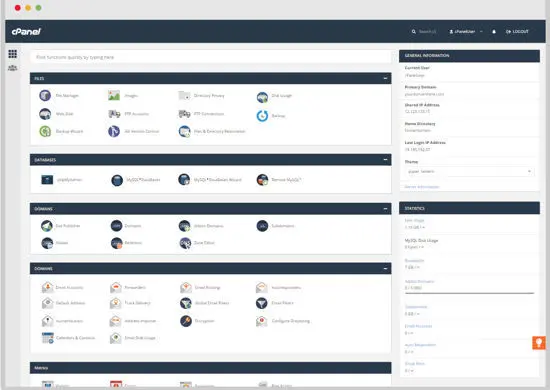
What is cPanel?
cPanel is a web hosting control panel software developed by cPanel, LLC. It provides a graphical interface and automation tools designed to simplify the process of hosting a web site to the website owner or the "end user". It enables administration through a standard web browser using a three-tier structure.
cPanel's Features
- Add and remove email accounts.
- Set up email forwarding, mailing lists and auto-responders.
- Manage spam filters and global filters.
- Encrypt emails for security.
- Read and compose emails anywhere in the world via Webmail.